Last week, the Republican Party of the United States exposed the personal voting information of 220 million registered voters on S3. Granting wide open permissions in S3 is a common occurrence in public cloud, and as an administrator I can attest to the fact that if you're not looking for it, you're almost certainly exposed in one area or another of your organization, and exploits are straightforward and well-known.
Luckily, the public cloud is CRAZY easy to automate. I've solved this problem for everyone everywhere, and all you need to do is download a simple bash script and run it on a regular basis using ansible.
Here's how it works:
- List all of your buckets in S3
- Surf those bucket's policies for "All User" access
- List all of your objects in S3
- Surf those object's policies for "All User" access
- report those results automatically using Ansible
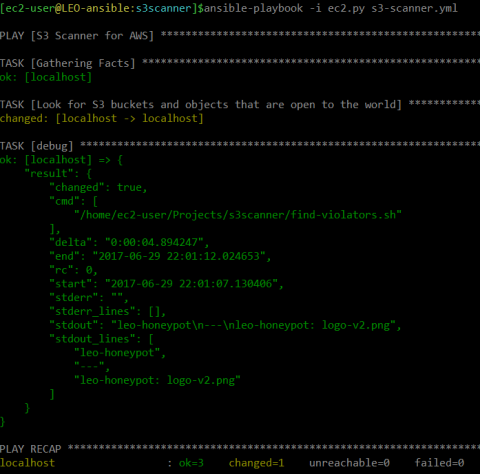
The JSON in the output at "stdout_lines" shows that I have both a bucket policy and an object policy that are open to the world. I could further use this information to either alert my security team, lock them down automatically, or both.
https://github.com/bkrubnzi/scripts/blob/master/find-s3-violators.sh
